Cheat Sheet: Identity Threat Detection & Response
The following vendors have been taken from The Cyber Hut’s Identity and Access Management Industry Analysis (IAM2) Map available here.
Vendors missing? Please contact us.
Drivers
Importance of identity and access management increasing - B2E, B2C, workload/NHI, AI-agents
IAM components now deployed in a broader array of locations - on-prem, virtual, containers, cloud service providers
Range of relying systems and applications broadening in type and volume - APIs, web, mobile, SaaS, custom
IAM attack surface increasing as a result
Many points of evidence for data breaches based on vulnerable IAM components - OWASP Top 10 #1 Broken Access Control, #5 Security Misconfiguration, #7 Authentication Failures and multiple from the likes of Mitre Att&ck including Phishing, Authentication Process Modification, Access Token Modification and more general Credential Access
Issues with visibility (due to isolated IAM components), threat analysis and integration with real time threat intelligence, behaviour monitoring and base-lining and lack of implementation of basic IAM controls such as hygiene and cleanup contribute to IAM related vulnerability exploitation
Sample Capabilities
Data Collection
auth source
IAM infrastructure - IDP, SSO, profile, permissions, activity, authentication and credentials usage, relying party usage, federated access
on-prem, cloud service provider, SaaS, private cloud
Human, workload and non-human identities too
Agent-less, API, flat file, extensible, OOTB accelerators to get started
Visibility
correlation and normalisation
single view across an entire life cycle of identity - perhaps including non-human activity too
risk and threat intelligence from known-knowns and also runtime dynamic attacks
linkages between session data and application activity
Detection
Rules and signatures
base-lining of behaviour
anomalous activity
comparison to real-time threat intelligence, campaigns and sector specific attacks
Remediation
Out of the box responses
Chatops integration
Semi-automated reporting / steps creation
Co-pilot and AI assisted response options
in-flight changes to things like sessions, permissions, deception, degradation, reporting, alerting
Sample Vendor Links & Descriptions
Anetac - “Discover. Monitor. Respond. Continuously discover, monitor, and respond to identity vulnerability surface and their access chains”
Authmind - “Hacker’s don’t hack in, they log in. Prevent your next identity-related cyberattack with the AuthMind Identity Security Platform. It works anywhere and deploys in minutes.”
Hydden - “Continuous, Proactive Identity Attack Surface Management for Hybrid IT Environments. Connect and contextualize identity data across any system or application to reveal and stop threats hiding in the shadows.”
Breez Security - “Revolutionizing cloud security with behavioral detection and identity-powered investigations. Eliminate blindspots with high fidelity detection. Save time/resources with one-click investigations”
Permiso - “Unified Identity Security. Risk and Threat Visibility”
Push Security - “Stop identity attacks and secure the new perimeter. The browser-based Identity Threat Detection & Response (ITDR) platform”
Reveal Security - “Attackers don't break in. They log in. Detect insider threats and identity-based attacks in applications and cloud.”
Rezonate - “Protect Identities, Everywhere. Use actionable insights and hyper-security automation to prevent account takeovers and privilege abuse, stop attacks in real time, and streamline compliance.”
Sharelock - “Revolutionizing Identity Security with Autonomous AI. Empowering proactive defense against identity threats with self-improving AI, perfectly integrating with diverse identity management systems for total digital protection.”
Silverfort - “Where Identity Protection Has Never Gone Before. On-prem, cloud, humans or machines, and everything in between”
Stack Identity - “Real-time access visibility, identity security, just-in-time provisioning, self-service, and automated controls—all in one platform.”
Unosecur - “Defend your cloud infrastructure from Identity Threats. The fastest way to visualize and understand Human and Non-Human Identities (NHIs). Quickly mitigate the most important identity threats in real-time. Zero disruption. Maximum Protection.”
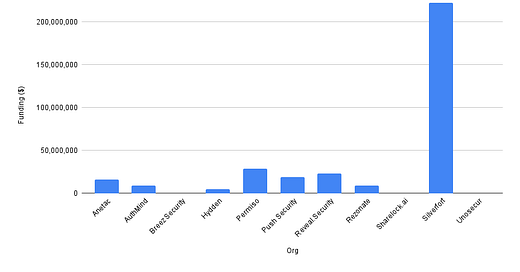
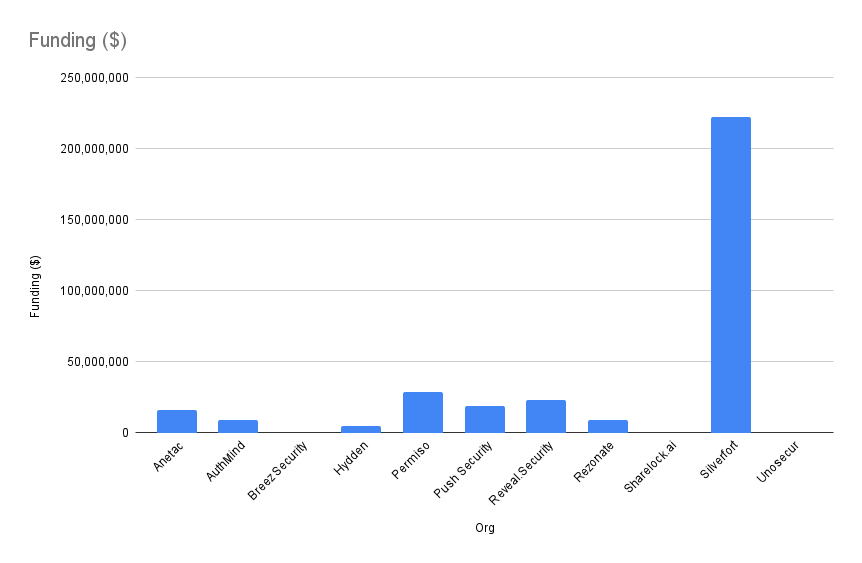
Vendor Funding
Data Source: Crunchbase / Company Website
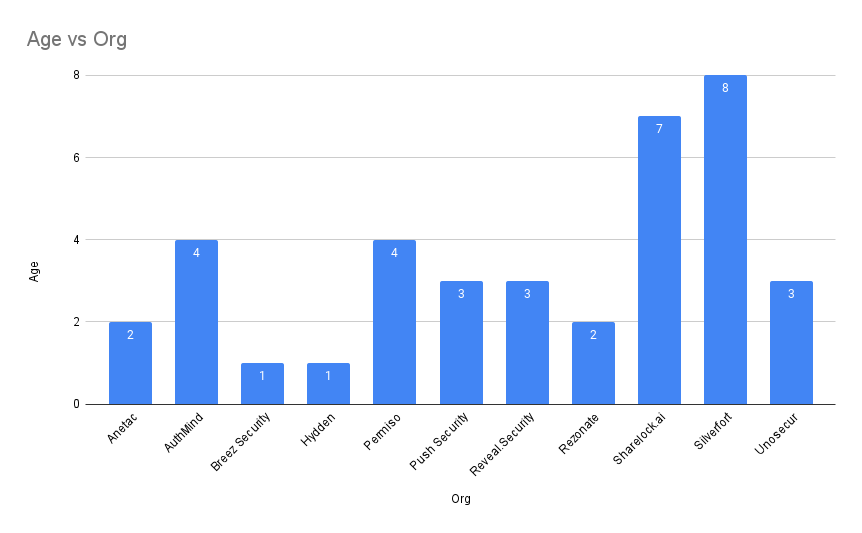
Vendor Age
Data Source: Crunchbase
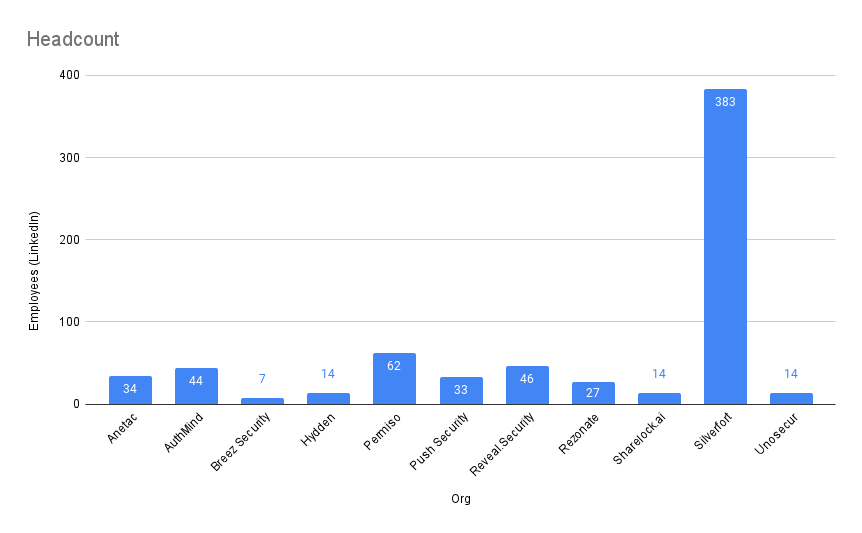
Vendor Headcount
Data Source: LinkedIn
Data last updated: Nov 2024.
Useful Further Links
The Cyber Hut TV Vendor Introduction Video Playlist
Book an analyst market inquiry
Follow The Cyber Hut on LinkedIn