Cheat Sheet: Non-Human Identity
The following vendors have been taken from The Cyber Hut’s Identity and Access Management Industry Analysis (IAM2) Map available here.
Vendors missing? Please contact us.
Sample Capabilities
Discovery of entities such as services, APIs, bots, process automation functions
Ability to tag and catalogue via flexible risk assessment methodology
Unique naming of entities
Creation and management of a NHI source of truth
Credential issuance to entities without human involvement
Authentication of entities without human involvement
Revocation of credentials issued to non-human entities
Behaviour monitoring of services and APIs
Linkage of entity creation to human interaction
Integration to CI/CD and DevOps tooling
Consistent policy based authentication and access control management
Integration scenarios for identity providers, key management systems and vaults
Dashboarding capabilities for activity and risk
Flexible deployment across cloud native, containers and PaaS
Sample Vendor Links & Descriptions
Aembit - “Replace manual and insecure access to non-human identities with our automated and secretless Workload IAM platform”
Astrix.Security - “Secure and govern service accounts, API keys, secrets, OAuth tokens and other NHIs across SaaS, Cloud and On-Prem environments”
Clutch.Security - “Securing Non-Human Identities. Everywhere. Know, Understand, Control, and Secure all Non-Human Identities Across the Entire Ecosystem”
Corsha - “Securely automate, move data, and connect with confidence from anywhere to anywhere”
Entro.Security - “A pioneer in non-human identity management, Entro enables organizations to securely utilize non-human identities and secrets, overseeing their usage and automating their lifecycle from inception to rotation”
Natoma - “Protect your Data & Systems from Unauthorized Non-Human Identities”
Oasis.Security - “Simple. Smart. Effective. Non Human Identity Management”
SPIRL - “Untangle the production identity mess with SPIRL. SSO for your workloads in minutes, no matter where they run. Fully compatible with existing IdPs, OAuth and mTLS”
Token.Security - “Token is the new approach designed forthe identity boom era. IntroducingMachine-First Identity Security”
TrustFour - “Workload Micro-Segmentation”
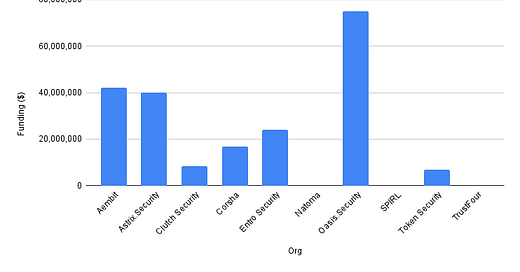
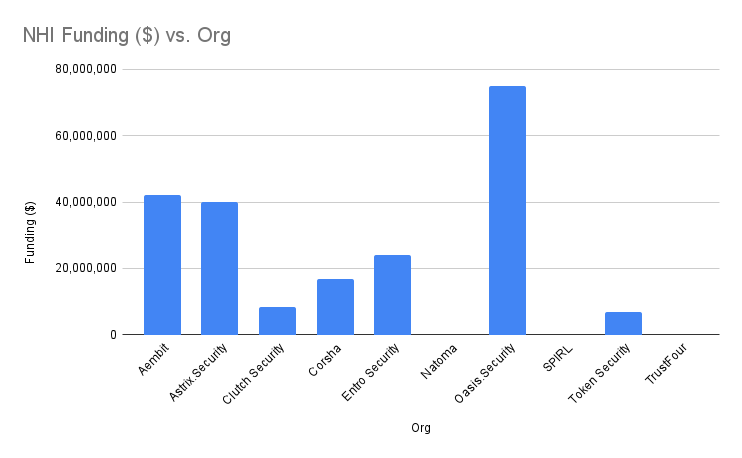
Vendor Funding
Data Source: Crunchbase
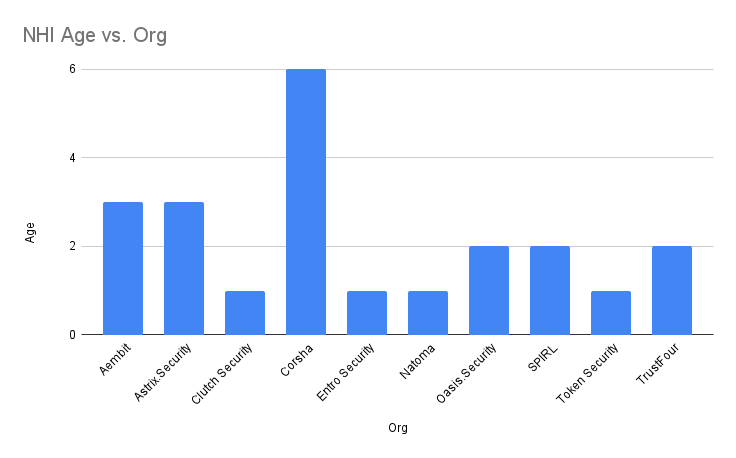
Vendor Age
Data Source: Crunchbase
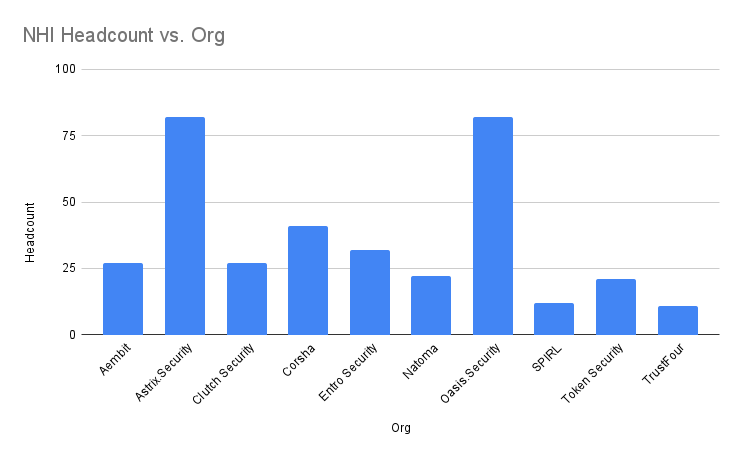
Vendor Headcount
Data Source: LinkedIn
Data last updated: September 2024. Clutch Security added Oct 2024.
Useful Further Links
The Cyber Hut TV Vendor Introduction Video Playlist
Book an analyst market inquiry
Follow The Cyber Hut on LinkedIn